BeginCTF2024 WP
最后更新时间:
页面浏览:加载中...
MISC:
问卷
real check in
使用CyberChef直接解:
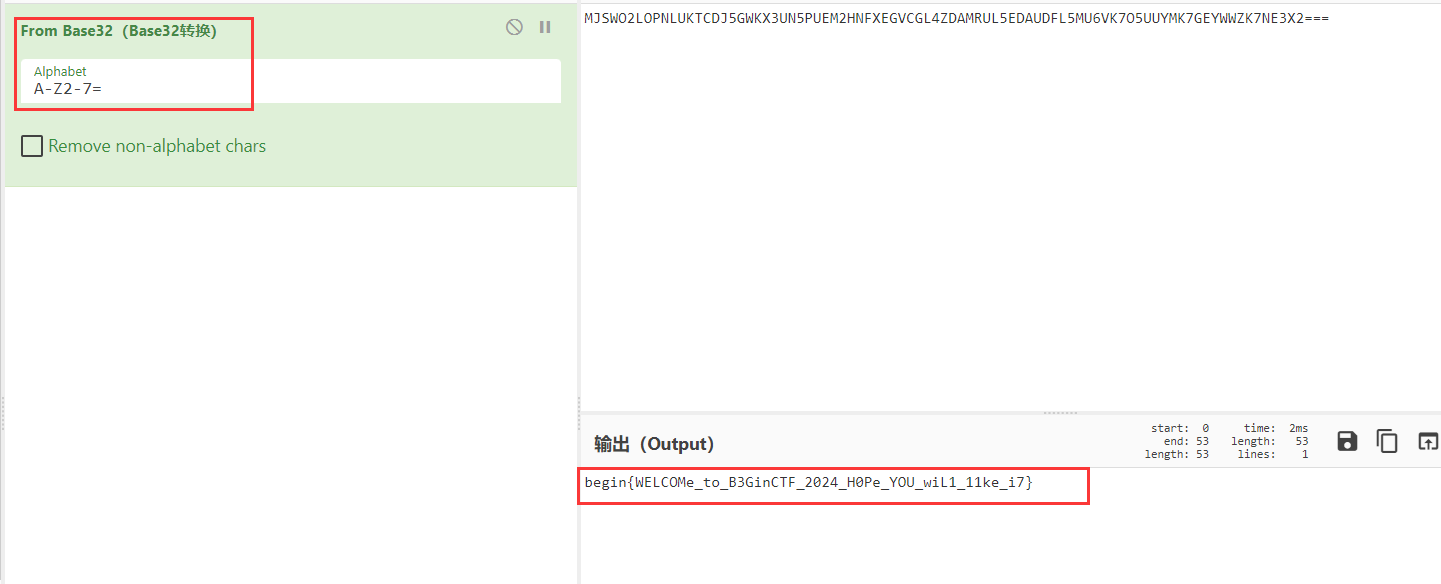
FLAG:begin{WELCOMe_to_B3GinCTF_2024_H0Pe_YOU_wiL1_11ke_i7}
Tupper
使用python脚本把所有文件内的字符按照文件顺序从小到大依次提取合并输出
1 | |
得到下面的值使用base64解码:
1 | |
解码得到:
1 | |
根据题目:tupper 自我指涉公式生成图片,使用的这个网站在线生成https://tuppers-formula.ovh/
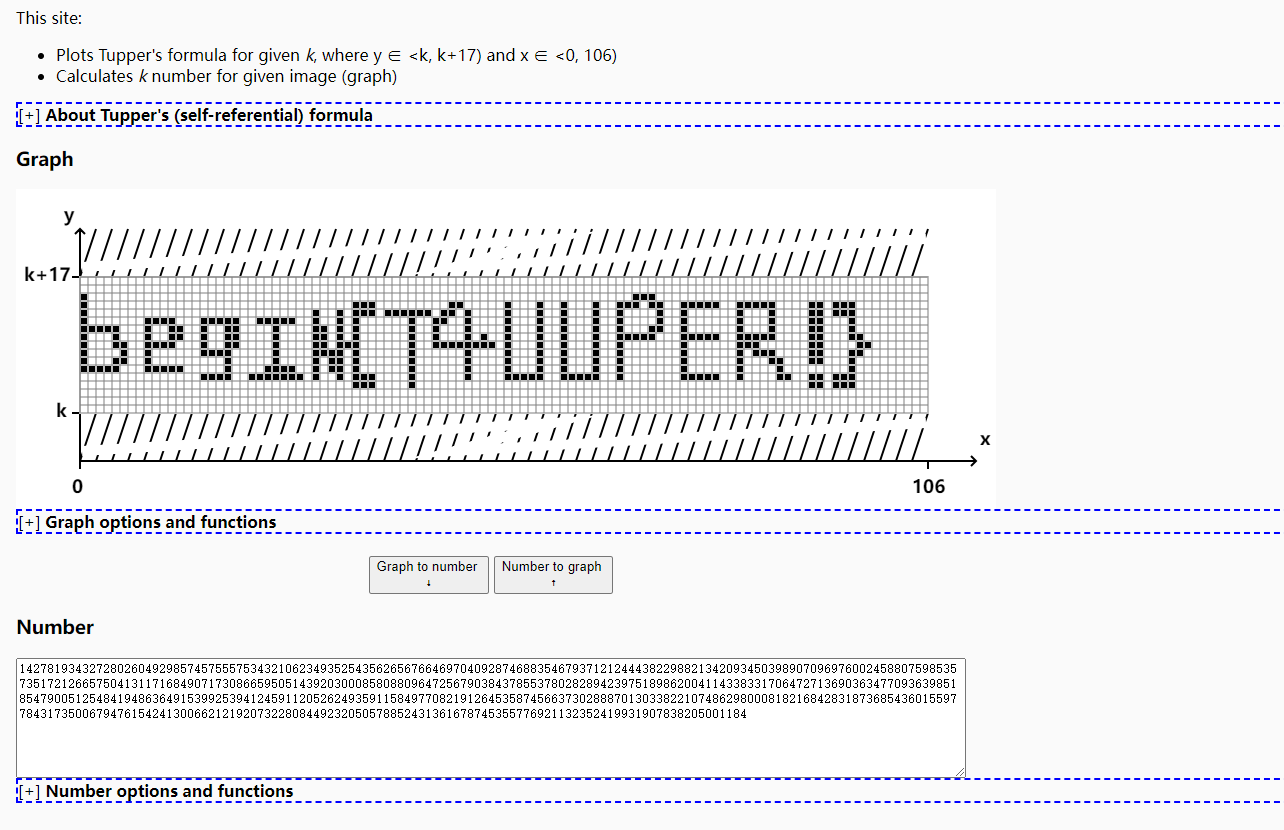
FLAG:begin{T4UUPER!}
where is crazyman v1.0
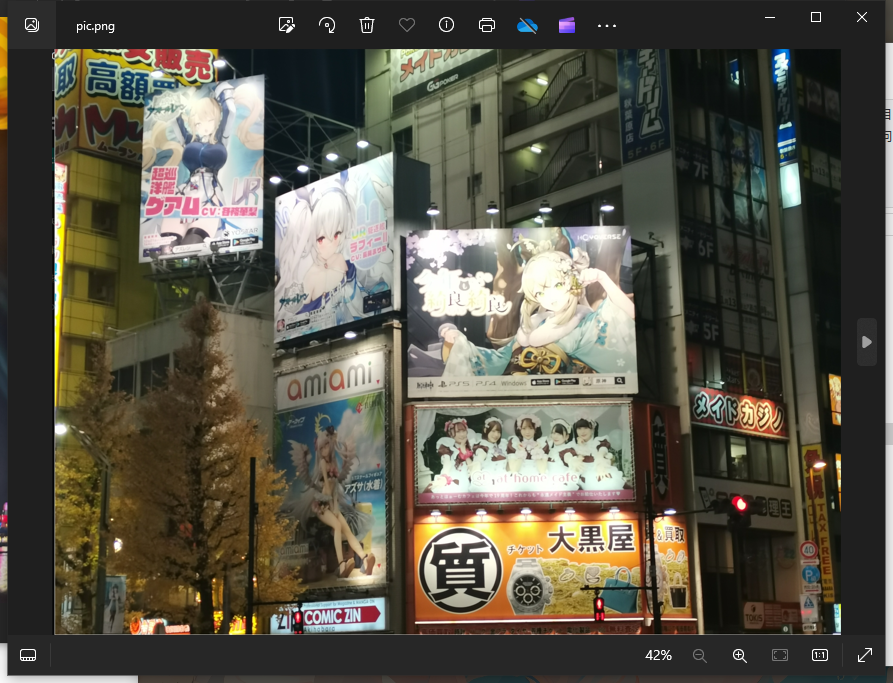
FLAG:begin{秋叶原}
where is crazyman v2.0
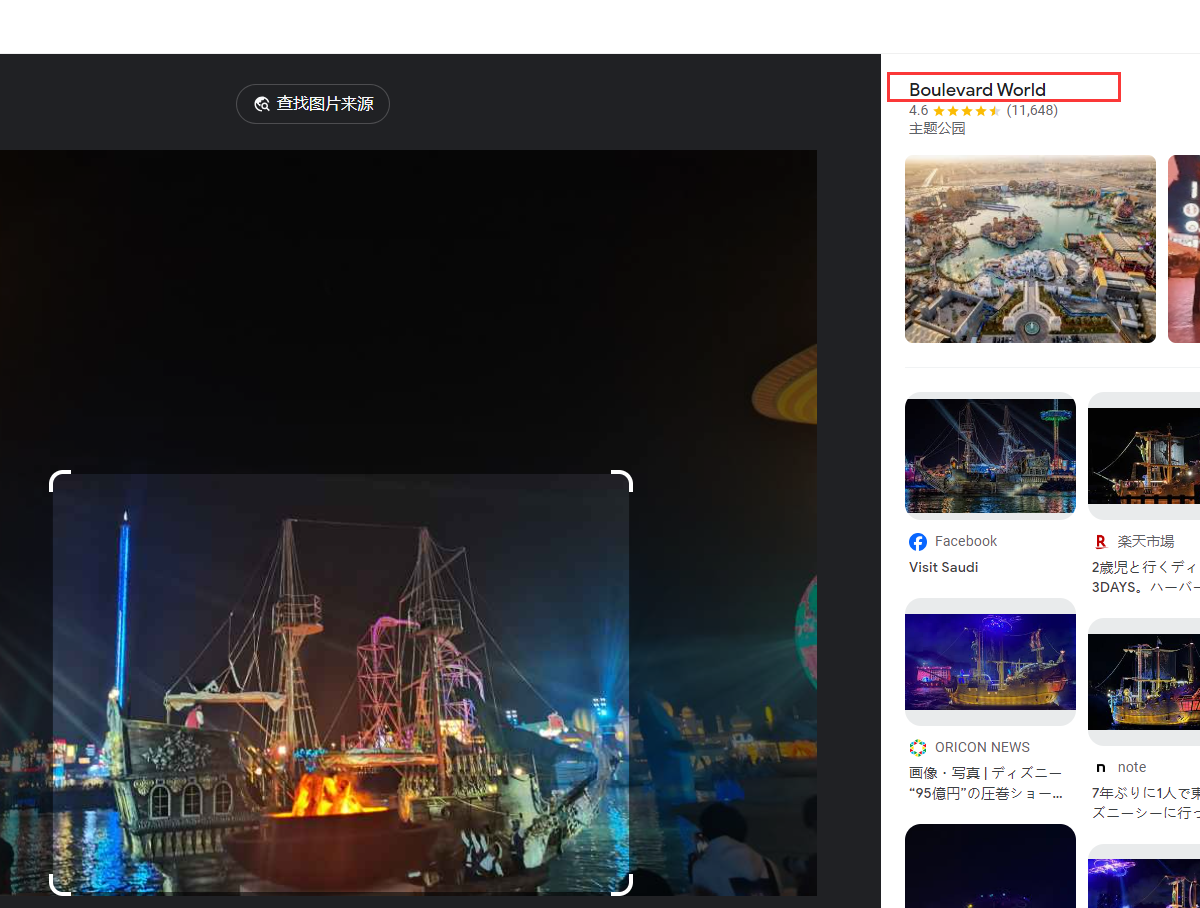
FLAG:begin{Boulevard World}
WEB:
zupload
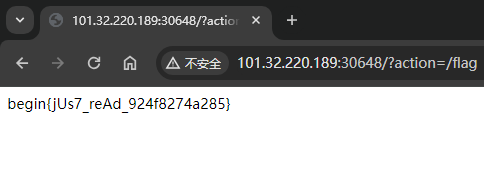
FLAG:begin{jUs7_reAd_924f8274a285}
Reverse:
real checkin xor
1 | |
解密程序
1 | |
FLAG:begin{3z_PY7hoN_r3V3rSE_For_TH3_Be9inNEr!}
Forensics:
逆向工程(reverse)入门指南
打开是PDF文件直接全选标注颜色发现上面有一块Ctrl+A全选
Ctrl+V复制到其他地方查看发现flag
1 | |
FLAG:begin{0kay_1_thiNK_YoU_Ar3_a1Re@DY_rE4D_6uiDe8ooK_AnD_9OT_FL46}
学取证咯 - cmd
执行:volatility_2.6_win64_standalone.exe -f 学取证咯.raw –profile=Win7SP1x64 cmdscan
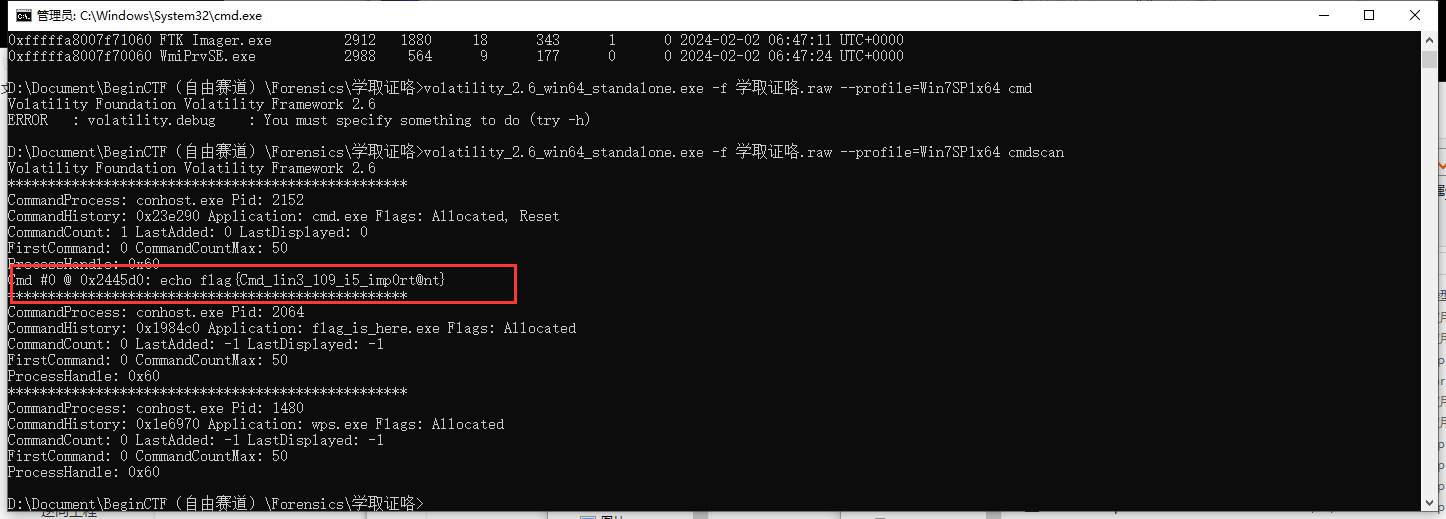
FLAG:begin{Cmd_1in3_109_i5_imp0rt@nt}
学取证咯 - 还记得ie吗?
开始使用
1 | |
并未找到flag
搜索教程中发现浏览器的历史记录有本地文件,使用
1 | |
查找浏览器的历史文件history文件夹相关文件
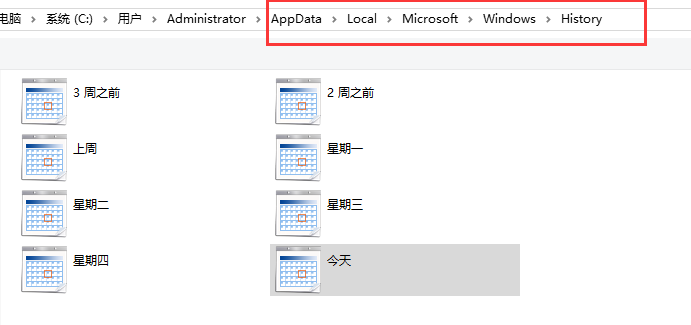
根据下图左侧的0x编号提取文件
1 | |
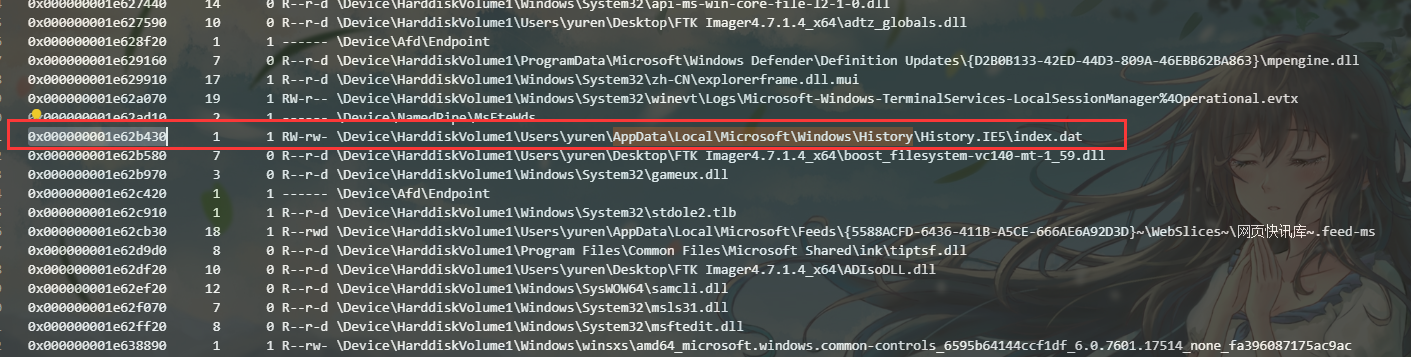
提取出来的bat文件改成txt搜索flag找到flag(顺便发现另一题的机密文件)
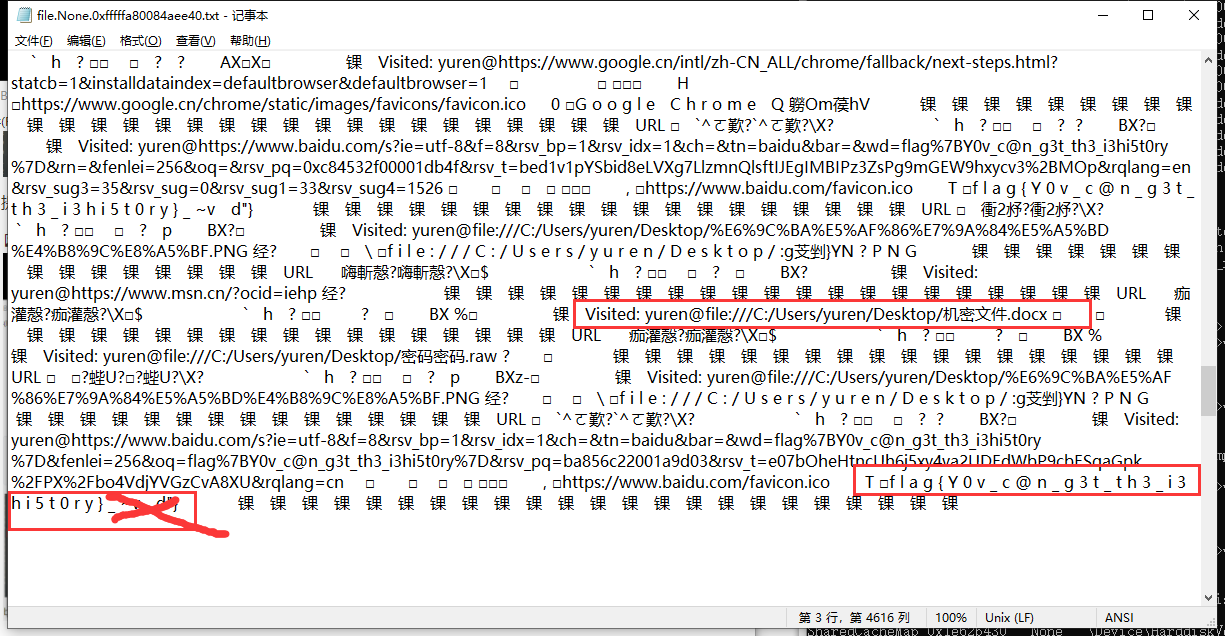
FLAG:begin{Y0v_c@n_g3t_th3_i3hi5t0ry}
学取证咯 - 机密文件
机密文件
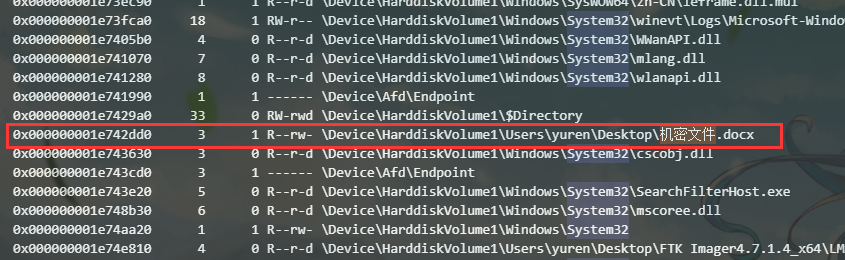
同样把文件提取出来改名字后缀直接打开得到flag
1 | |
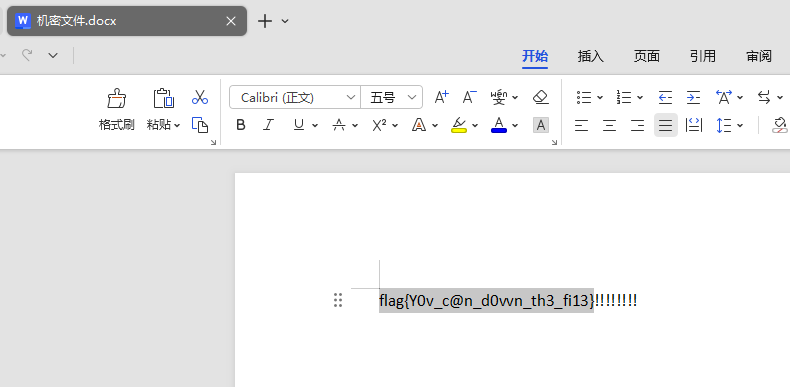
FLAG:begin{Y0v_c@n_d0vvn_th3_fi13}